The State of AI in Cybersecurity 2023: The “Lake Wobegon Effect”
Discover a pervasive “Lake Wobegon Effect,” where enterprises overestimate their capabilities to manage IT infrastructure.
For nearly 50 years, Minnesota Public Radio featured a weekly variety show called A Prairie Home Companion, which itself featured a recurring segment called News from Lake Wobegon — a fictional small town in Minnesota, in which “all the women are strong, all the men are good-looking, and all the children are above average.”
From this, we get the so-called “Lake Wobegon effect,” a phrase that captures the natural human tendency to overestimate our capabilities and achievements relative to others. (Based on more than a decade of teaching graduate-level courses in quantifying security-related risks, I can attest that students are notoriously overconfident in their ability to estimate — a perfect example of this pervasive phenomenon.)
We can see the Lake Wobegon effect play out in Aberdeen’s recent study on The State of AI in 2023, in which respondents were asked to self-rate several aspects of their IT infrastructure capabilities using the following maturity class framework:
- Basic: Manual processes, commonly spreadsheet-based that do not fully meet business needs
- Functional: Processes that meet simple business needs but with little standardization
- Intermediate: Standardized processes that meet expectations, supported by some automation
- Advanced: Standardized processes that exceed expectations, supported by end-to-end automation
- Optimized: Standardized processes involving advanced analytics and AI to enable easier innovation and agility
See More: The State of AI in Cybersecurity 2023: The Good News — and Some Ongoing Challenges
Suppose you’re already familiar with the Lake Wobegon effect. In that case, you probably won’t be surprised to learn that the responses were skewed pretty strongly toward the Advanced / Optimized side of the scale, as opposed to the Basic / Functional side, as shown in the Table below:
Figure 1: Self-ratings for maturity class skew positive — but most likely are overly optimistic
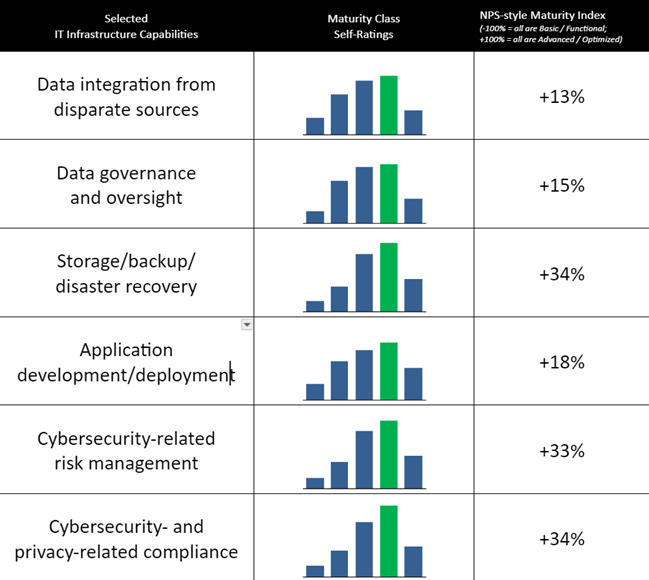
Source: State of AI 2023 Aberdeen, October 2023
On the other hand, respondents should always be taken at their word. Without question, we can stipulate that Aberdeen doesn’t have sufficient first-hand knowledge of these nearly 350 organizations to refute their self-ratings — but most likely, they’re overly positive. As one compelling piece of evidence: Consider that as a group, respondents were strongly positive about the maturity of their cybersecurity-related risk management capabilities — and yet the full range of responses for their estimated year-over-year change in performance illustrates the reality of cybersecurity winners and losers, with respect to two key objectives that are held by virtually all enterprise cybersecurity initiatives:
-
- Reducing the frequency of data loss or exposure of enterprise data (e.g., records, files, and intellectual property) and
- Reducing the frequency of unplanned downtime or slowdown of enterprise systems (including endpoints, networks, and back-end servers, applications, databases, and cloud-based services).
Said another way: The top performers are generally characterized by a year-over-year reduction in the frequency of these undesirable outcomes — while for all others, the year-over-year frequency in these areas ranged from about the same to much higher. See Figure 1, below.
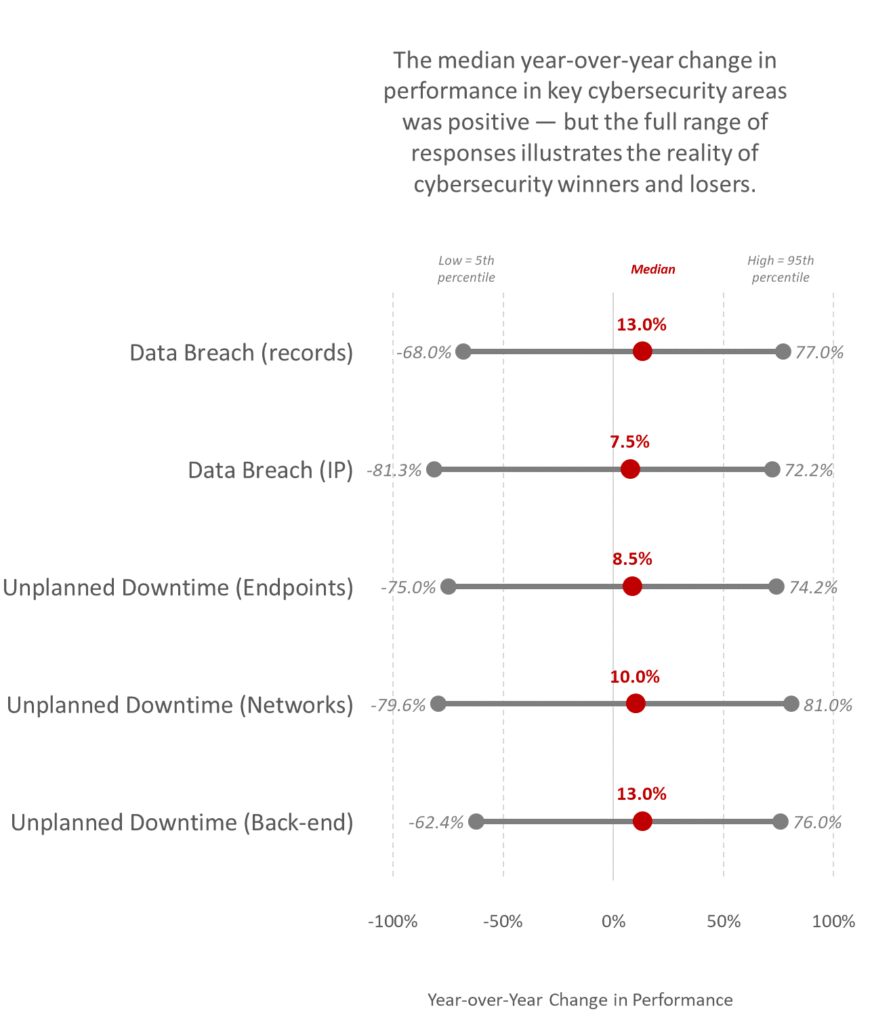
Figure 1: The range of change in performance for two key objectives of enterprise cybersecurity initiatives illustrates the reality of cybersecurity winners and losers
Source: State of AI 2023 Aberdeen, October 2023
Overall, Aberdeen’s research confirms the interest and optimism for expanding the use of AI and analytics in cybersecurity —but hopefully, these insights from The State of IT 2023 dataset about current capabilities can also help tech pros to keep enterprise expectations about AI from getting too far ahead of reality.
In the next two blogs in this 4-part series about AI in cybersecurity, we’ll look at Aberdeen’s research findings about the leading use cases and solution categories.
How accurate are your cybersecurity perceptions? Let us know on Facebook, X, and LinkedIn. We’d love to hear from you!
Image Source: Shutterstock
MORE ON AI IN CYBERSECURITY
- 5 Predictions for Generative AI Attacks and 5 Defense Strategies
- AI: The Wakeup Call to Improve Open-Source Software Security
- Mitigating AI Risks: Protecting from Identity Theft, Deepfakes, and Fraud
- Cybersecurity and AI/ML, Before the New Age of AI: Insider Risk
- Cybersecurity and AI/ML, Before the New Age of AI: Bad Bot Detection and Mitigation







