NISTIR 8286A Risk Management Guidance Part 2: Tools and Insights to Manage Risks
After learning to integrate cyber risk management with enterprise risk management and defining information resource categories in Part 1, here’s guidance on executing and implementing risk registers.
This is the second of a three-part article series describing the execution and implementation of risk assessment, including tools for assessing and tracking risk.
In the first installment of this three-part series, I described how to integrate cyber security risk management (CSRM) into the overall enterprise risk management (ERM) processes, as described in NISTIR 8286A Identifying and Estimating Cybersecurity Risk for Enterprise Risk Management. This leads to documenting risk appetite and risk tolerance. This article explains how to use risk registers and supporting tools to manage risk identified in system risk assessments.
The Complete Risk Management Process
The risk appetite and tolerance documentation begins the risk management process, as shown in Figure 1. Note that all risk management activities start with management categorizing information resources and identifying each resource’s appropriate risk tolerance level. These and the following steps are taken at specific levels of the enterprise.

Figure 1: Risk Management Process (from NISTIR 8286A)
C-level executives and enterprise risk managers define risk appetite at a high level. Data owners translate this into risk tolerance and work closely with the security team to implement appropriate safeguards. This is the point at which risk is assessed, tracked, and managed: providing a feedback loop to C-level for making appropriate changes based on the ever-changing risk profile.
See More: NISTIR 8286A Risk Management Guidance Part 1: Risk Appetite and Risk Tolerance
Residual risk
Once security applies initial controls based on risk tolerance, each system conducts a risk assessment. Regardless of the safeguards applied, the residual risk still exists. Residual risk is the risk remaining after implementation of safeguards that is based on three variables:
- The data owner’s decision about how to manage the risk
- The changing threat landscape
- Emerging vulnerabilities
Residual risk begins at an acceptable level based on tolerance, but it usually changes over time. This is why we perform regular risk assessments. The organization should track all risks in a risk register, even currently acceptable risks.
Implementing a summary risk register
Figure 2 shows part of a risk register for quantitative or hybrid risk assessments. The columns not shown allow for assigning responsibility and tracking management efforts. You can download it as an Excel spreadsheet. This register is based on the recommended document in NISTIR 8286A, but I adjusted it to manage and reflect tolerance more clearly.
- Description is a description of the potential risk.
- Category is a value from Table 1 included in the Risk Register workbook and is modifiable to meet unique organizational needs; placing a value here automatically enters a value in the Tolerance column
- Likelihood is the probability that the risk will be incurred; for example, once every five years would have a value of 20%
- Impact is the impact of a single event, which can be actual (quantitative) or estimated (hybrid)
- Before Tolerance is the automatically calculated annualized impact due to the incident (LIKELIHOOD * IMPACT)
- After Tolerance is an annualized impact value that can represent various things based on how the register is used; here, it represents the impact the data owner is willing to accept (BEFORE TOLERANCE * TOLERANCE)
- Variable values in Table 2, also included with the register, are used to automatically flag After Tolerance risk values as LOW (green), MEDIUM (yellow), or HIGH (red)

Figure 2: Sample Summary Risk Register

Table 1: Tolerance Values Set for Each System
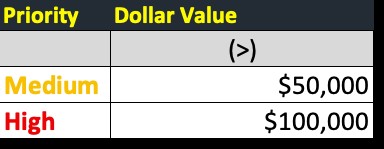
Table 2
Each system should have its risk register. Security teams work with data owners to set Tables 1 and 2. Note that risk 5 has two category values that apply to confidentiality and availability. Many identified risks will probably affect multiple elements of the CIA triad.
This approach to a register is not intended to represent business impact accurately. Instead, it is intended to show the severity of a risk-based on data owner tolerance for risk. It is simply a tool used by a knowledgeable team for risk tracking and tolerance adjustment.
See More: Why Cyber Risk Management Is Key To Uncovering Security Holes in Your Network
Supporting detailed risk record
A summary risk register is a good tool for working with management to deal with risk discovered during assessments. However, it is often insufficient when technical teams need a good understanding of the risk and the appropriate controls.
Also included with the downloadable Risk Register tool is a sheet, as shown in Figure 3, that enables detailed information about the risk listed in the risk register. Each entry in the register should also include a detailed risk sheet. The detailed document consists of the information gathered during a risk assessment.

Figure 3: Detailed Risk Record
Final Thoughts
So far in this series, we have looked at the first steps in a risk management process. These steps include
- Integrating cyber risk management with enterprise risk management
- Defining information resource categories
- Defining C-level appetite for risk by resource category
- Working with data owners to create risk tolerances for systems for which they are responsible
- Creating a risk register for each assessed system to be used during a risk assessment
The next steps, performing a risk assessment and managing the discovered risk, are covered in this series’s third and final article.
Does your organization maintain a risk register to evaluate risks? Comment below or let us know on LinkedIn, Twitter, or Facebook. We’d love to hear from you!
MORE ON RISK MANAGEMENT:








