Average Ransomware Payout Touched $312K in 2020, Up From $115K in 2019
The average ransomware payout crossed the $300,000 mark in 2020 with organizations paying up to regain access to their data and sustain operations in a pandemic-infested business climate.
The average ransomware payment increased by 171% to over $300,000 in 2020, a report by the Unit 42 of Palo Alto Networks, and the Crypsis Group has revealed. Manufacturing and professional & legal services led the list of the most-affected sectors, with the highest ransomware payout clocking as much as $10 million last year.
The average ransom paid by victims of ransomware attacks shot up by 171% in 2020, a study by Unit 42, Palo Alto Networks’ threat intelligence arm found. The year-over-year surge was the highest in the history of ransomware payouts, with the average ransom payout clocking $312,493, up from $115,123 in 2019.
The highest ransom paid by organizations doubled from $5 million in 2019 to $10 million in 2020 as well. Correspondingly, Unit 42’s 2021 Ransomware Threat Report notes that ransom demand also displayed a marked increase – peaking at $30 million compared to $15 million in 2019.
The sharp rise in ransom demand and payments made by victim organizations is not a new phenomenon but has been a trend over the years. What set last year’s figures apart was that the outbreak of the novel coronavirus, which caused a global pandemic, allowed threat actors to arm twist organizations into complying with their demands.
“Ransomware operators were brazen in their attacks in an attempt to make as much money as possible, knowing that healthcare organizations—which needed to continue operating to treat COVID-19 patients and help save lives—couldn’t afford to have their systems locked out and would be more likely to pay a ransom,” Palo Alto Networks said.
Unsurprisingly, healthcare was the most targeted sector in 2020. The fact that healthcare organizations store Personal Healthcare Information (PHI) of a large number of people and many of these organizations still use legacy IT networks marred by security holes, make them highly vulnerable to targeted ransomware attacks.
The Ryuk ransomware gang, which netted $150 million in ransom payments, is reportedly behind the largest number of attacks targeting healthcare organizations.
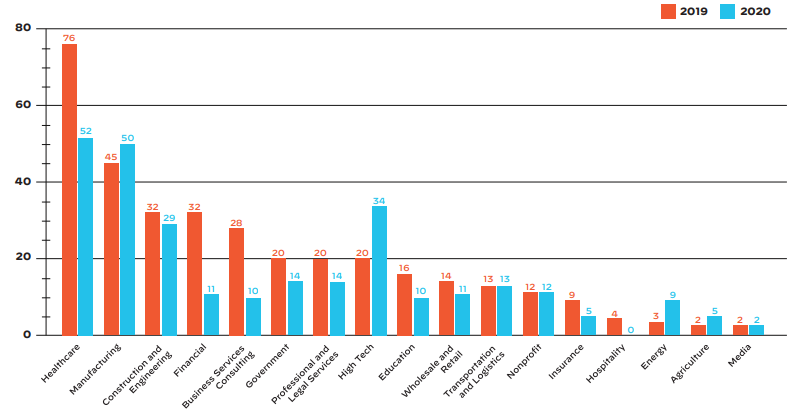
Source: Palo Alto Networks | Ransomware Incident Response Cases by Industry (US, Canada, and Europe)
However, the most targeted sector wasn’t necessarily the most affected. According to Palo Alto Networks, manufacturing, professional & legal services, and construction were the sectors that saw the highest number of organizations becoming victims of ransomware attacks and data leaks.
This is a new attack vector – dubbed Double Extortion – wherein the attackers, upon gaining access to victim systems and networks, exfiltrate data before encrypting it for a ransom. This way, even if the victim organization performs a restoration of their IT infrastructure through backups and refuses to pay the ransom (cash or Bitcoin), the attackers still hold leverage over victims by threatening to publish or sell stolen data.
“Many of the operators have staged leaks of each organization’s data, likely in an effort to pressure victim organizations into paying the ransom by a deadline, failing which the operators decide to leak the full data. Published data from each organization ranged anywhere from 30 MB to more than 1000 GB,” the firm said.
This attack method was pioneered by the operators of Maze ransomware strain, who announced retirement back in November 2020.
See Also: 5 Reasons Why Your Business Should Have a Ransomware Plan in 2021

Numbers of Victim Organizations with Data Leaked Globally by Sector
The ransomware gang responsible for the largest number of attacks in 2020 was NetWalker (114 organizations victimized), followed by RagnarLocker, DoppelPaymer, Nefilim, Darkside, and REvil/Sodinokibi. Data from January 2021 shows that NetWalker is also behind a third (33%) of all data leaks under the double extortion attack method.

Number of Victim Organizations Globally by Ransomware Family that had their Data Published on Leak Sites
Thankfully, NetWalker operations were disrupted in January this year in an international operation spearheaded by the FBI. According to the U.S. Department of Justice, the operation resulted in the confiscation of nearly $454,500 in Bitcoin, the seizure of a dark web hidden resource in Bulgaria which was used by the operators of NetWalker to communicate with victims, and the indictment of a Canadian national who allegedly earned more than $27 million as an affiliate of the ransomware gang. Threat from other ransomware variants, however, still looms large.
See Also: Why Tech Leaders Shouldn’t Ignore a Problem Like Ransomware
What The Future Looks Like
Wendi Whitmore, Senior Vice President at Palo Alto Networks, said, “Attackers got greedier, richer and more technically savvy and invested profits into R&D, developing the scale and hacking techniques that enable them to move at lightning speed to exploit new vulnerabilities.”
The Santa Clara-headquartered company expects the following trends to evolve in the ransomware operations industry in the coming years:
- Double Extortion
- Ransomware-as-a-Service (RaaS)
- Newer Ransomware Variants
- Even Higher Ransom Demands
- Reliability on Familiar Tools (such as Cobalt Strike, PowerShell Empire, and PowerSploit)
The 2021 Unit 42 Ransomware Threat Report was authored by Palo Alto Networks along with incident response, risk management, and digital forensic service provider Crypsis Group. The report is based on data collated from ransomware leak site data available on the dark web as well as public websites, global threat data available via internal and external sources, breach response data by the Crypsis Group of 252 ransomware leak sites, 337 victims, 56 industries, 5 global regions, and 39 countries. The report’s findings were also derived from 19,568 network sessions, and 164 unique malware samples.
Of all countries studied, the United States was found to have the highest number of ransomware attack victims (151 organizations). Canada is at a distant second with 39 organizations, followed by Germany (26), United Kingdom (17), France (16), and India (11).
Let us know if you liked this news on LinkedIn, Twitter, or Facebook. We would love to hear from you!








